Learn In-
Demand Skills for Tomorrow's Jobs
Experience learning that delivers results. We're disrupting the way you learn new-age technologies and we'll help you get job-ready, fast.


Industry-Recognized Excellence With Us.
Welcome to Totally Learn, your ultimate destination for skill development, professional growth, and lifelong learning.
MORE THAN 1,300 CUSTOMERS TRUST Totally learn






Courses Popular
-
152 Lessons
-
79 Lessons
-
137 Lessons
-
74 Lessons
Microsoft-AWS-GCP Cloud Computing -
-
79 Lessons
-
137 Lessons
-
74 Lessons
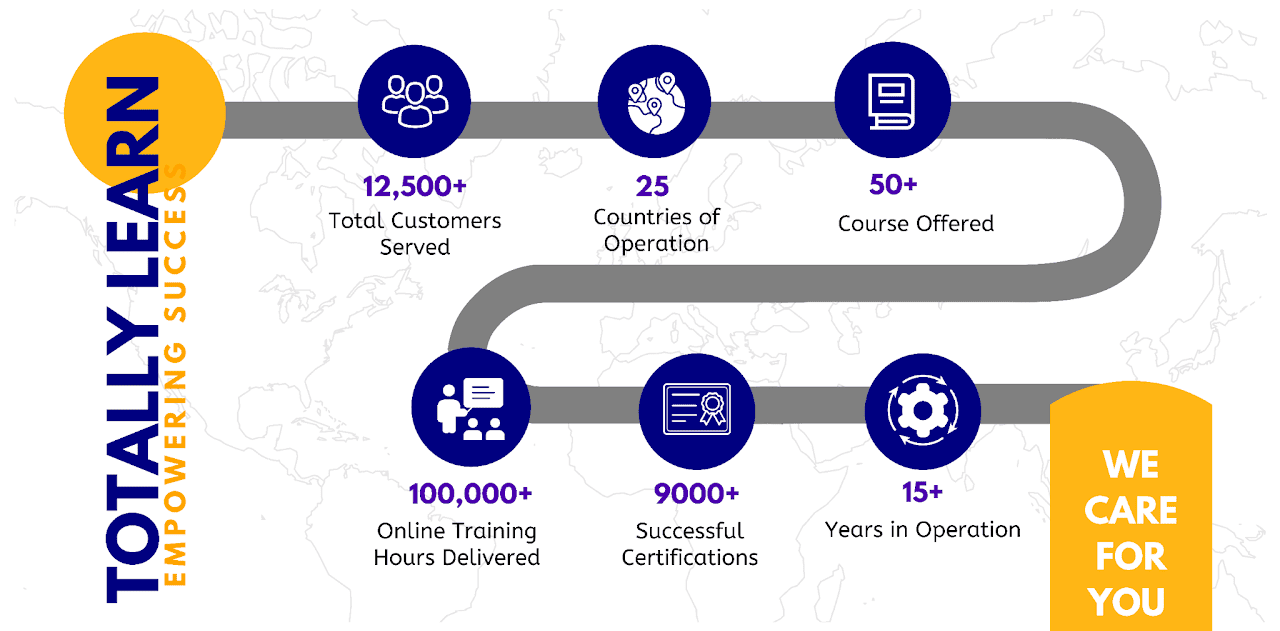
Empowering Success: A Global Impact in Training and Certification

Save BIG on Microsoft, CompTIA, AWS Exams with Totally Learn
Events Upcoming
Upcoming Education Events to feed your brain.
News Latest
-
-
December 22, 2025
-
-
September 17, 2025
-
-
August 7, 2025
What Candidate Think about Totally Learn?

Thanks to the PMP training from this company, I was able to secure a high-paying project management job within weeks of passing the exam!

The AWS certification training provided by this company was excellent. I was able to apply my new skills to real-world scenarios right away

The Azure certification training was challenging, but the instructors made it easy to understand. I would recommend this company to anyone looking to expand their IT skills.

The CEH training I received from this company helped me take my career in cybersecurity to the next level. I feel confident in my abilities and am grateful for the quality training.
















